aisikl
Registered
hello there
ever since i'm using Macosx, i've been ssh-ing in my home comp from work (i work in networking and it's very usefull to have a workstation in another domain to do tests from) -- anyway: i made sure that the connection is secure because a lot of classified data is going thru the lines --
until this happened:
today i was chatting with a friend -- i was explaining him why i liked macosx so much and as an example told him to ftp as visitor in my comp.
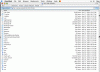
i did the same in the command line and didn't really notice anything odd until my friend told me to log in through a web browser - i did so in omniweb and to my utter astonishment and shock it showed me everthing: etc, var, usr, mach, mach.sys, mach_kernel (see attachment) --
i did the same in explorer and opera and there it didn't show me all the hidden system files --
can anybody please tell me how bad this is?
thanks
['aisikl]
ps: don't bother ftp'ing into my ip (it's dynamic and will have changed by the time you try it)
ever since i'm using Macosx, i've been ssh-ing in my home comp from work (i work in networking and it's very usefull to have a workstation in another domain to do tests from) -- anyway: i made sure that the connection is secure because a lot of classified data is going thru the lines --
until this happened:
today i was chatting with a friend -- i was explaining him why i liked macosx so much and as an example told him to ftp as visitor in my comp.
i did the same in the command line and didn't really notice anything odd until my friend told me to log in through a web browser - i did so in omniweb and to my utter astonishment and shock it showed me everthing: etc, var, usr, mach, mach.sys, mach_kernel (see attachment) --
i did the same in explorer and opera and there it didn't show me all the hidden system files --
can anybody please tell me how bad this is?
thanks
['aisikl]
ps: don't bother ftp'ing into my ip (it's dynamic and will have changed by the time you try it)